Written by ContentPowered.com
Written by ContentPowered.com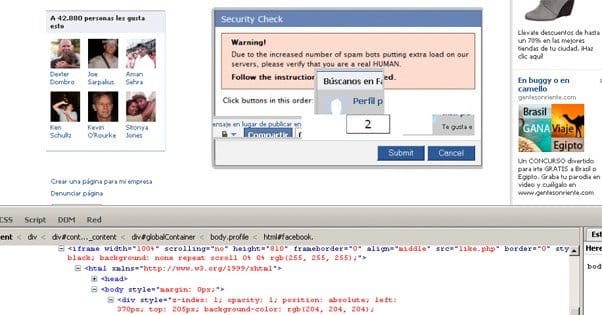
There’s a darker side to social marketing, and I’m not talking about gray market traffic sales and untargeted followers. I’m talking about the truly black hat exploits, the hacks in code that trap traffic and make them Like a Facebook page – or perform any other social engagement shy of commenting – without realizing it.
When I say this, I can already hear some people talking about those shady apps that require shares on different networks to enter a contest or claim a prize. Apps that try to post to your wall when you like a page, or apps that require a like to read an ebook, and the like. These are not what I’m talking about because, at the end of the day, you can see what’s going on. You can read the fine print or see the window that pops up to make the post for you. You can even set the apps to personal privacy so that, even though they post to your wall, no one but you can see those posts.
No, what I’m talking about it much more sinister. I’m talking about sites where you try to click a button or a video play and nothing happens, so you click again and now it works. Sure, that may seem like lag or an unresponsive video player, but it could also be an attempt to clickjack. So what is clickjacking specifically, how does it work, and how can you put a stop to it?
What is Click or Like Jacking
Clickjacking is a generic term for any script or hidden exploit that redirects a click from its intended use to an unintended use. For example, if you were to try to click a link on a page and instead an entirely different page appeared, that would be a clickjack. The simplest example would be an invisible site-wide overlay that hijacks the first click a user makes and uses it to open an ad or confirm some dialogue box.
A likejack is the same thing, only with a more specific purpose. Rather than redirecting the click to any potential purpose, a likejack forces the user to like a Facebook page. This requires that the user be logged in to Facebook, but these days, who isn’t?
So how do these things work? There’s a lot of complex code at the heart of the issue, and some of it can get very technical. Usually the easiest method people use for the attack is to install a transparent iframe on top of content on a website. It’s invisible to the user, who browses your page as they normally would. When they click on something, though, that click is stolen to the purpose of the clickjacker, and the iframe disappears. You just feel as though your click got lost or your mouse just didn’t register the click, so you click again. The second click works and you move on, none the wiser.
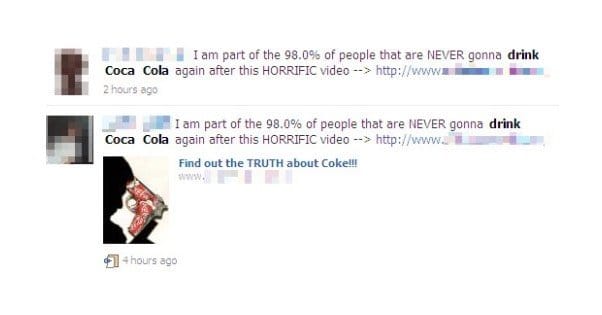
Most of the time, when you see someone who has posted out of character on Facebook and then claims they were hacked, it’s just a simple clickjack. No access to their account is necessary. All they did was be tricked by a clickbait site and click on it anywhere, which shared the post on their wall. Everyone has seen someone on their list do this at some point, and usually the victim overreacts thinking they were hacked. They change passwords, they audit apps, they call tech support, and it’s all in vain. Their information wasn’t stolen, they just shared the post unwittingly.
If you were to make the invisible iframe visible, you might see something like this. A video player with two play locations, one in the center of the video and one in the lower left corner. Both locations are covered by Facebook like buttons or, in some cases, post share buttons. The user doesn’t see them and clicks to try to play the video, and are thus sharing and propagating the bait. It’s all similar in many ways to parasitic organisms in real life, which infect the host and drive them to do things that increase the likelihood of the parasite being able to infect other organisms at the end of its life cycle.
There are also more malicious versions of the clickjack out there. In a paper published by two Carnegie Mellon scholars, a proof of concept setup was created that allowed an attacker to steal personal information from Facebook upon a stolen click. It also used a Facebook like button that, rather than attempting to predict where the user would click like in the video example, simply followed the mouse cursor. This can be performed with Twitter as well.
The level of malicious detail in the attack depends on the purpose of the hacker. It can be exploited simply to increase followers on a page or make a particular message go viral in a spammy way. It can be used to harvest personal information of users, whatever is publicly accessible on Facebook specifically.
Now, when it comes to protection against clickjacking and likejacking, there are two sides to the issue. On one hand, you have users, who are the targets of clickjacking and who suffer the most from the abuse. They need to take steps to protect themselves from the issue. On the other side, you have site owners. There aren’t as many steps you can take to prevent clickjacking from the webmaster side, but there are a few, so I’ve compiled them for your use.
Protecting Yourself as a User
From the user side, many of these tips come down to intelligent behavior online. Unfortunately, all too many people get too complacent while they browse and decide some things just aren’t worth the effort. The reality is they tend to not be punished for it, either. Even though there are a lot of different threats out there, there are also a lot of different people, and the two groups don’t necessarily meet at a 1:1 basis. Some people seem to stumble into threats on a daily basis – talk to any tech support person and you’ll hear the stories – while others happily browse completely unprotected and live a charmed and completely safe life.
Still, as a web browser, you should implement at least some of these tips. Remember; software can only do so much. A good sense of skepticism and some common sense will go a long way where software won’t reach.
1: Audit your likes. This is just good practice, but it will also tell you if you’ve ever been the victim of clickjacking before. Sometimes, honestly, it’s quite hard to tell. If the person using the exploit doesn’t post much, you might never see their posts, so you wouldn’t see anything strange.
To audit your likes, go to Facebook, click your name to go to your own profile page, and scroll down. On the left side, you will eventually see a box labeled Likes. Click it and you will see all the pages you have liked. Here you can set whether or not you like them, whether or not you’re following them, and what you want to do about it.
2: Audit your apps. This is similar to auditing likes, because one purpose of clickjacking is to authorize an app to post for you, so you don’t need to be hijacked every time the malicious user wants you to post for them. To audit your apps, go to Facebook and click the drop-down arrow in the upper right. In the menu, click settings. On this page, on the left sidebar, you will see “apps.” Click it to see a list of all the apps you have authorized to use your account.
Here, you can edit the ability of an app to post on your behalf, restricting who can see it. You can change this between everyone, just friends, only yourself, or a custom audience. You can also remove an app, which removes its ability to post for you, but does not remove any data the company behind the app might have. Fortunately, there’s not necessarily a lot they can do with that information.
When you remove an app, there is a checkbox that will remove any posts made by that app from your timeline and history. If you’re removing a normal app you just don’t use, it doesn’t matter. However, if you’re removing a spammer’s app, you might want to use this to make sure no one browsing your timeline can fall victim.
Note: There is an option for disabling apps entirely. If you don’t think you will ever use Facebook apps, on or off site, you can disable them without consequence. Just remember that this will remove your ability to claim offers or enter contests run through Facebook, as well as use apps like other social site integration.
3: Hide personal information from non-friends. This is another change you can make from the settings menu. Click on the privacy option in the sidebar, and you can change both who can see your posts and who can look you up via methods like your name, email address, and phone number. By setting stricter privacy settings, you make it harder for clickjackers to steal personal information about you.
4: Avoid clicking on suspicious sites. This is where so many people fail, because of psychology and clickbait. Spam posts with clickjacking attached really don’t look a lot different from normal clickbait spam from sites like Buzzfeed and Upworthy. You just need to exercise caution. If it’s a site you’ve never heard of, or if it looks like it was coded by a third grader, maybe consider not clicking to try to play the video. Also, familiarize yourself with how the YouTube player actually looks, and don’t click to play a video using a player that doesn’t look right.
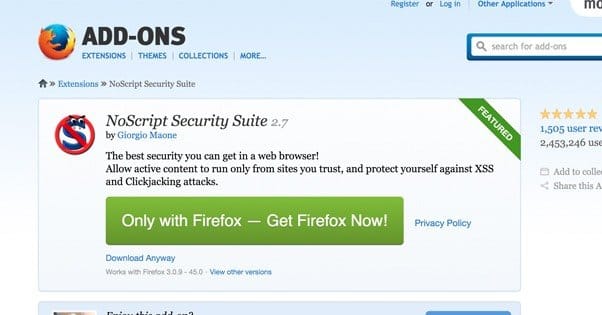
5: Use NoScript and AdBlock. These are two browser plugins that will help keep you safe for a number of reasons.
AdBlock comes in many forms. AdBlock Plus is one of the most popular options, but I’ve found it to be a bit of a resource hog. I prefer uBlock Origin, these days. It blocks ads and scripts, and allows me to block specific elements of a site, as well as whitelisting sites I want to support.
NoScript is a more general block-all-scripts browser extension that disables anything from running if you don’t want it to. This includes Javascript and Flash, so if you want to watch web videos, you will have to disable it temporarily. However, even with the general filters disabled, NoScript has a clickjack detector that’s always on.
6: Keep an antivirus installed and updated. This is common sense for any user who uses an internet-enabled computer. All viruses and malwares are bad, but some of them will install computer-side clickjacks that will hijack your data and do other terrible things. An up to date virus program will keep these at bay.
7: Sign out of Facebook on the web. When you’re done with Facebook, log out. This is unfortunately only useful if you don’t tend to go back and forth between Facebook and other sites. Still, if you don’t think you’re going to browse Facebook again right away, sign out. It can’t hurt.
Protecting Yourself as a Webmaster
As I mentioned, most webmasters don’t have much they can do to prevent clickjacking. There are essentially two ways a site can be clickjacked; on-site and off-site. On-site involves your site being compromised and clickjacking code added to it. Off-site involves another domain loading your site in an iframe and layering their clickjack over top of it. This is more difficult to deal with, but possible.
1: Install security plugins or software. This is especially necessary if you use WordPress or another extensible, popular CMS. The more popular the architecture, the more likely you are to face common exploits. Keeping your software up to date and installing additional security will dramatically lessen the potential for you to be compromised and have malicious code added to your site.
2: Make sure passwords are secure. This is generally good advice for everyone in every situation. Use secure passwords to avoid having them guessed or brute forced to gain access to your site. Make sure you’re using strong, different passwords for different sites. If you can’t manage to remember that many unique passwords, get a password manager that will handle them for you while you remember one master password.
3: Audit your site for potential malicious code. One warning sign you might encounter is being removed from the Google index due to malicious code being detected. You might also want to check access logs to see if your server was accessed from anywhere other than your home IP.
4: Use a frame busting script. A frame buster is a bit of code that you put on your website that detects if the site is being opened through a frame. If it detects a frame, it forces the site to reload and put the user on your actual site, rather than the frame site. It makes it much more difficult for a clickjacker to actually implement their iframe hack.
5: Implement X-Frame options. X-frame options are defenses you can implement to protect a site against frames and clickjacking, but they are significantly more technical. They also only work in the most modern browsers, so old browser users are out of luck.
With all of this in place, your site should be much more resilient against potential clickjacking. Combine it with monitoring and you’ll be able to detect when you’re the target, and can help prevent clickjackers from stealing your traffic in a malicious way.